Runtime communication security
We carefully created the runtime architecture with your security in mind. Because the runtime can reside in your network or can be hosted in our data center, Boomi provides extensive security measures, both internally and in our data center, to prevent any compromise in your data or the runtime.
During installation, no third-party software is installed with the runtime except in the case noted. The data center verifies and authenticates all installations and downloads before deployment.
After deploying the runtime behind the firewall, the runtime is in continuous contact with the data center for tracking and status information. You do not need to open any inbound firewall ports for the runtime to communicate with the data center because the runtime initiates all communication to the data center. The runtime always starts the connection, so the data center never sends data from the data center to the runtime. When the runtime initiates the connection to the data center, it always authenticates it before sending data using an SSL handshake. It uses the digital certificate automatically created during registration (see Password Encryption Security).
The communication security protocol:
-
All communication from the runtime to the data center uses TLS version 1.2 encryption.
-
All outbound communication from the to the data center is HTTPS, port 443.
-
The uses a standard TLS handshake to authenticate with
platform.boomi.com.
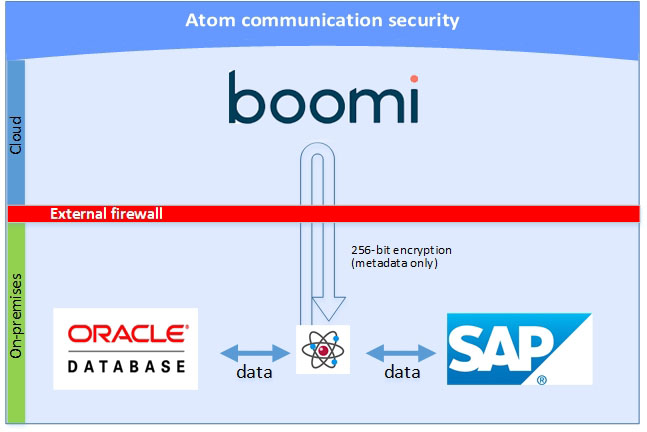
The runtime communicates information to Integration in two modes: ongoing or automatic communications and user-initiated communications. As stated previously, production data is never sent to the data center unless explicitly configured by the Integration user, for example if the runtime is hosted versus downloaded. The runtime does not transport any information to the data center without explicit request by the user.
The following information is transmitted to the data center automatically by the runtime:
-
Online Status — The runtime communicates on an ongoing basis with the data center to indicate its status. This ensures uptime of any deployed runtime, and the Integration service knows in a short time frame if the runtime goes offline for any reason.
-
Tracking Information — File name, directory, and so on of the files processed (if applicable) as well as success and failure counts, process runs, and so on.
-
Integration Process Updates — The runtime periodically checks for and applies any updates to the configuration of the integration processes made by the user.
-
Runtime Updates — The runtime periodically checks for and applies any updates to the runtime code itself.
The runtime transmits the following information to the data center upon request by a user:
-
Logging Information — Information about running a specific integration process. The total run time, along with logging for each step in the process, and error messages that pertain to a run failure, if one occurred.
-
Error Details — A detailed error message explaining what the error was that caused a specific run of an integration process to fail.
-
Connector browsing (for specific connectors) — For example, when building processes, it can transmit database schema information to define the field mapping rules. It only sends schema information, and no actual data.
