Converting from custom to HIGH security policies
Using Boomi's HIGH security policy and configuring any customizations with the Atom Security Policies object ensures that you automatically receive the new policy changes from Boomi without having to make manual changes to your custom security files.
About this task
Configuring custom security policies by using a separate CUSTOM policy file has been deprecated as of June 2023. Use the steps in this topic to convert to a HIGH security policy and then use the Atom Security Policies object to manage any required customizations.
Procedure
-
Identify which containers are configured to use CUSTOM security policy files by using the Boomi UI or the Platform API.
-
In the Platform, go to Manage > Runtime Management, and for each runtime cluster and runtime cloud, go to the Properties panel, Advanced tab and look for the property Security Policy with a CUSTOM value.
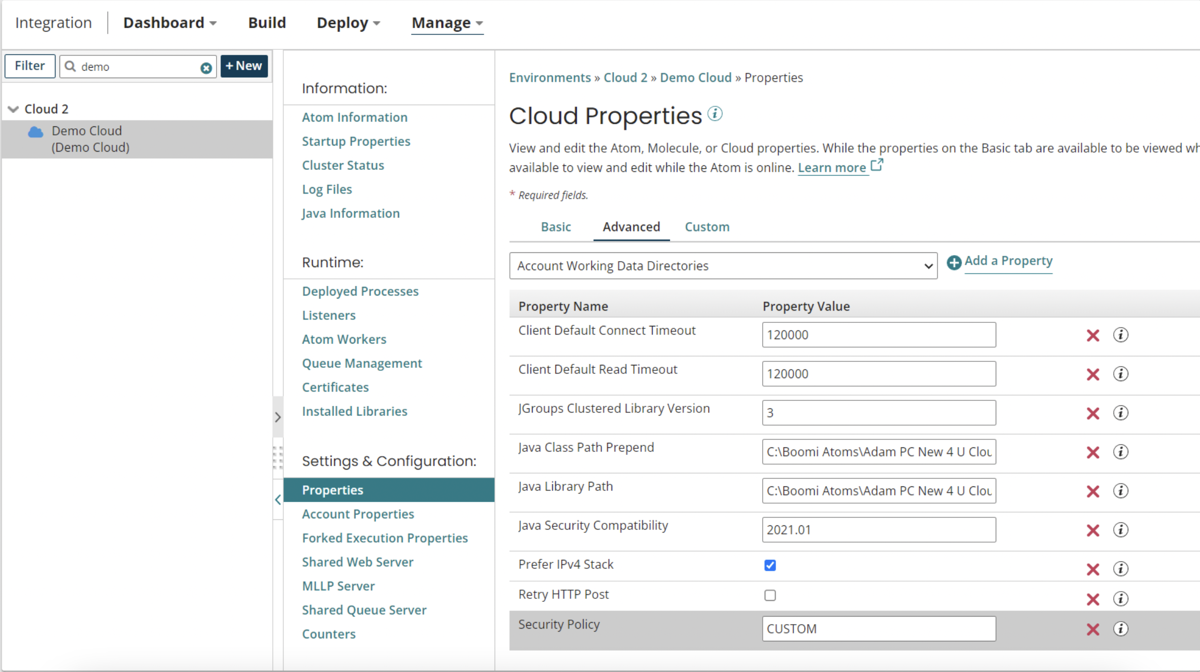
-
Using the Platform API, first use the Atom object to query
type="CLOUD"ortype="MOLECULE. Then for each runtime cluster and runtime cloud, use the Atom Startup Properties object to retrieve the runtime's properties. Look forsecurityPolicyLevel="CUSTOM".
-
-
For each runtime that uses a CUSTOM policy, identify which permissions are customized in each policy file.
- Obtain the custom policy files from the local runtime's <ATOM_ROOT>/bin directory: procbrowser-CUSTOM.policy, procrunner-CUSTOM.policy, and procworker-CUSTOM.policy.
noteBy convention, custom changes are typically organized under the
//customsection of the files, however this is not required. You can use a text diff utility to identify all of the differences between your files and Boomi's standard policy files. -
Use the UPDATE operation of the Atom Security Policies object to customize the HIGH security policy with your existing custom policies. See the example in the following section.
-
In Runtime Management, on the Properties panel, Advanced tab, set the Security Policy property to HIGH.
-
Restart the runtime cluster or runtime cloud for the changes to take effect.
noteIf you automate provisioning for your containers, be sure to modify any scripts or other assets to change the security policy property to HIGH and use the API to make any custom changes.
Configuring using Atom Security Policies object
The following example shows how a custom policy set by using the CUSTOM file can be configured by using the Atom Security Policies object:
Custom Policy File
In this snippet of an example policy file, there is a custom policy to grant permission to a local directory, my/Custom/Dir:
{ATOM_ROOT}/bin/procrunner-CUSTOM.policy
...
...
grant {
…
// misc other permissions
permission java.lang.RuntimePermission "accessDeclaredMembers";
permission java.lang.RuntimePermission "instantiateClassLoader";
permission java.lang.RuntimePermission "setContextClassLoader";
// custom permissions
permission java.io.FilePermission "/my/Custom/Dir", "read,write,delete";
};
...
...
REST API Request example
You can use the UPDATE operation of the Atom Security Policies object to configure a HIGH security policy with the custom permissions in the example code snippet above:
POST https://api.boomi.com/api/rest/v1/ACCOUNT_ID/AtomSecurityPolicies/CONTAINER_ID
<bns:AtomSecurityPolicies xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:bns="http://api.platform.boomi.com/" atomId="CONTAINER_ID">
<bns:common/>
<bns:policies privilegeType="java.io.FilePermission">
<bns:arguments value="/my/Custom/Dir"/>
<bns:arguments value="read,write,delete"/>
</bns:policies>
</bns:common>
<bns:runner/>
<bns:worker/>
<bns:browser/>
</bns:AtomSecurityPolicies>
The Atom Security Policies object allows you to configure custom policies for the individual JVM types (runner, worker, and browser), however it is most typical to configure the policies by using the common section to apply to all three types.
